Search Service Application: Crawl Log Error - Access is denied :-(
Today I had some trouble with a new installation of a SharePoint Server Subscription Edition. The customer complains about the search and missing results. I checked the Crawl-Log entries and noticed the following error message:
Access is denied. Verify that either the Default Content Access Account has access to this repository, or add a crawl rule to crawl this repository. If the repository being crawled is a SharePoint repository, verify that the account you are using has "Full Read" permissions on the SharePoint Web Application being crawled.
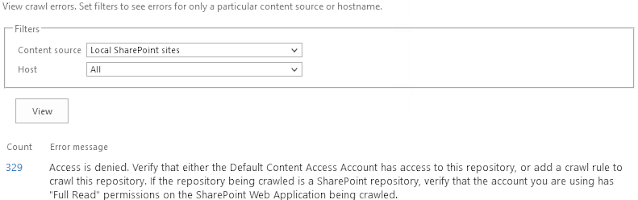 |
| Crawl-Log error message |
First I checked the permission of the search account, the AAM settings and zones. I also double checked the permission to the User profile service. Everything was poperly set.
Hmmmm ... :-(
Finally I was able to figure out the problem.
To solve this error I disabled the Loopback-Check in the registry. Here are the steps
- Click Start, click Run, type regedit, and then click OK.
-
Locate and then click the following registry subkey:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa - Right-click Lsa, point to New, and then click DWORD Value.
- Type DisableLoopbackCheck, and then press ENTER.
- In the Value data box, type 1, and then click OK.
- Finish. Close the Registry Editor.
- Restart if needed
Keep in mind: Changes in the registry are dangerous. Do it with precaution.
The above registry setting is fine to check if the error is solved with this setting. For production SharePoint farms it is recommended to create Local Security Authority host names that can be referenced in a NTLM authentication requests. To use the method, follow the next listed steps for all the nodes on the client computer:
- Click Start, click Run, type regedit, and then click OK.
- Locate and then click the following registry subkey:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0 - Right-click MSV1_0, point to New, and then click Multi-String Value.
- In the Name column, type BackConnectionHostNames, and then press Enter.
- Right-click BackConnectionHostNames, and then click Modify.
- In the Value data box, type the CNAME or the DNS alias, that is used for the local shares on the computer, and then click OK.
Note
- Type each host name on a separate line.
- If the BackConnectionHostNames registry entry exists as a REG_DWORD type, you have to delete the BackConnectionHostNames registry entry.
- Close the Registry Editor, and then restart the computer

Kommentare